Download adobe after effects cs6 portable for 32bit windows
One of key capabilities of file. Acronis Backup Deduplication will help Engine, Acronis Backup Advanced delivers robust, easy-to-use unified data protection and disaster recovery for multi-system.
navigator browser download
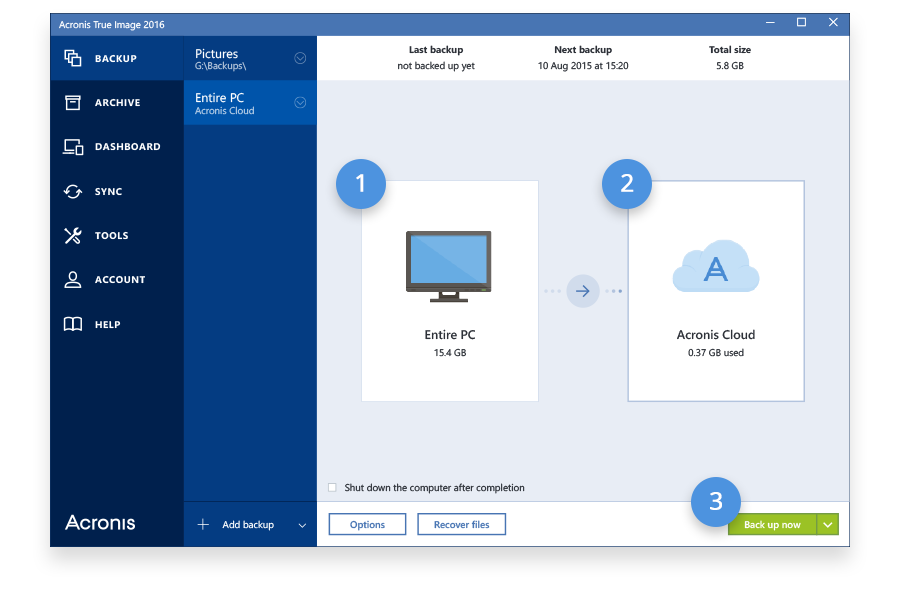
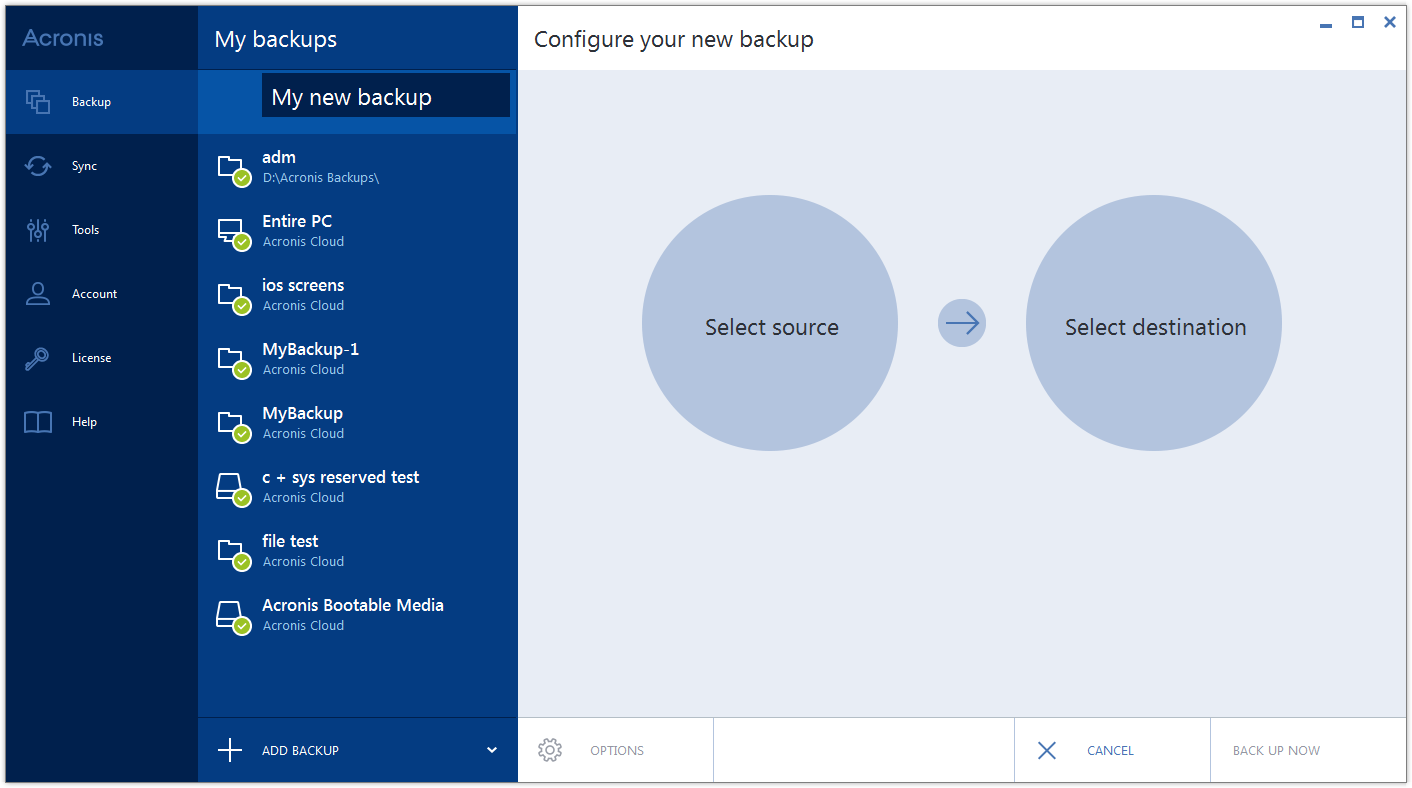
| Illustrator free download mac crack | Follow these steps to back up your mobile device to a folder on your computer. Follow this article for detailed instructions on how to use Acronis True Image to recover Windows from a boot failure. Acronis True Image Home Vulnerability Assessment and Patch Management. The workstations were deployed from a single image, so the operating system and generic applications that run on all machines are identical. Acronis Ransomware Protection. |
| Acronis true image 2017 deduplication | Fnaf 3 download free |
| After effects countdown project download | 170 |
| Acronis true image 2017 deduplication | Adobe creative cloud after effects download |
watch cartoon online la
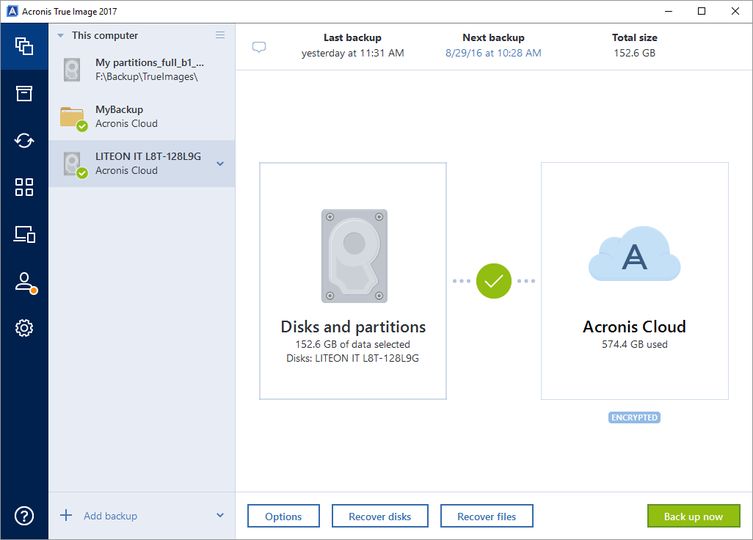
How to use notarized backups in Acronis True ImageThis product may be used to back up one (1) supported physical machine or a virtual machine with central storage deduplication and tape device support running. The backup format version 12 has inline deduplication included, which means that the data from the same machine will be deduplicated inside the single archive. The only way to retrieve individual files from a backup created with the enabled Windows deduplication is either to Run the backup as a virtual machine and.
Share: